A security loophole that would allow someone to add extra steps to the counter on your Fitbit monitor might seem harmless. But researchers say it points to the broader risks that come with technology’s embedding into the nooks of our lives.
On Tuesday, a group of computer security researchers at the University of Michigan and the University of South Carolina will demonstrate that they have found a vulnerability that allows them to take control of or surreptitiously influence devices through the tiny accelerometers that are standard components in consumer products like smartphones, fitness monitors and even automobiles.
In their paper, the researchers describe how they added fake steps to a Fitbit fitness monitor and played a “malicious” music file from the speaker of a smartphone to control the phone’s accelerometer. That allowed them to interfere with software that relies on the smartphone, like an app used to pilot a radio-controlled toy car.
“It’s like the opera singer who hits the note to break a wine glass, only in our case, we can spell out words” and enter commands rather than just shut down the phone, said Kevin Fu, an author of the paper, who is also an associate professor of electrical engineering and computer science at the University of Michigan and the chief executive of Virta Labs, a company that focuses on cybersecurity in health care. “You can think of it as a musical virus.”
The flaw, which the researchers found in more than half of the 20 commercial brands from five chip makers they tested, illustrates the security challenges that have emerged as robots and other kinds of digital appliances have begun to move around in the world.
With dozens of start-ups and large transportation companies pushing to develop self-driving cars and trucks, undetected vulnerabilities that might allow an attacker to remotely control vehicles are an unnerving possibility.
Still, computer security researchers said the discovery was not a sky-is-falling bug but rather a revealing window into the cybersecurity challenges inherent in complex systems in which analog and digital components can interact in unexpected ways.
“The whole world of security is about unintended interactions,” said Paul Kocher, a cryptographer and a former executive at the chip company Rambus.
Accelerometers are instruments that measure acceleration and are frequently manufactured as silicon chip-based devices known as microelectromechanical systems, or MEMS. Accelerometers are used for navigating, for determining the orientation of a tablet computer and for measuring distance traveled in fitness monitors such as Fitbits.
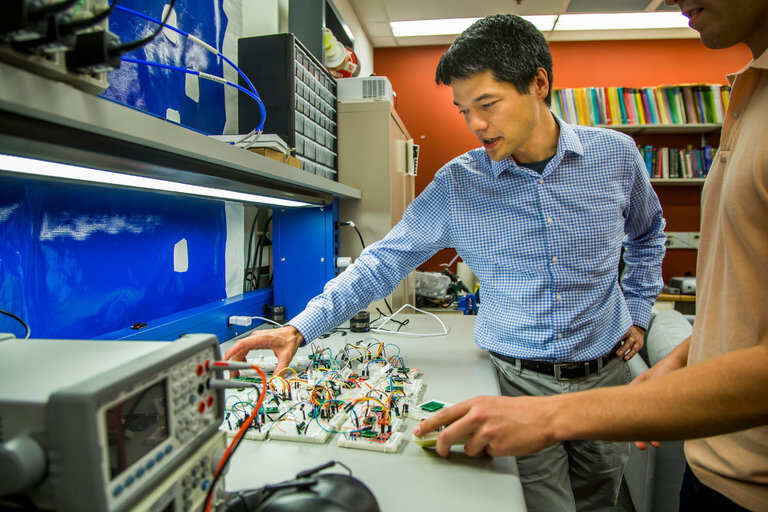
In the case of the toy car, the researchers did not actually compromise the car’s microprocessor, but they controlled the car by forcing the accelerometer to produce false readings. They exploited the fact that a smartphone application relies on the accelerometer to control the car.
While toy cars might seem like trivial examples, there are other, darker possibilities. If an accelerometer was designed to control the automation of insulin dosage in a diabetic patient, for example, that might make it possible to tamper with the system that controlled the correct dosage.
Dr. Fu has researched the cybersecurity risks of medical devices, including a demonstration of the potential to wirelessly introduce fatal heart rhythms into a pacemaker.
He said the current research was inspired by a discussion in his group about a previous study in which drones were disabled with music. He added that earlier research demonstrated denial-of-service attacks that used sound to disable accelerometers.
In 2014, security researchers at Stanford University demonstrated how an accelerometer could be used surreptitiously as a rudimentary microphone, for example. And in 2011, a group from the Massachusetts Institute of Technology and the Georgia Institute of Technology demonstrated the use of an accelerometer in a smartphone to decode roughly 80 percent of the words being typed on a nearby computer keyboard by capturing vibrations from the keyboard.
In the case of the research by the University of Michigan and the University of South Carolina, scientists stopped the accelerometer from functioning and changed its behavior.
In testing 20 accelerometer models from five manufacturers, they affected the information or output from 75 percent of the devices tested and controlled the output in 65 percent of the devices.
The Department of Homeland Security was expected to issue a security advisory alert Tuesday for chips produced by the semiconductor companies documented in the paper, Dr. Fu said. The five chip makers were Analog Devices, Bosch, InvenSense, Murata Manufacturing and STMicroelectronics.
The paper, which will be presented at the IEEE European Symposium on Security and Privacy in Paris next month, also documents hardware and software changes manufacturers could make to protect against the flaws the researchers discovered.
On Tuesday, a group of computer security researchers at the University of Michigan and the University of South Carolina will demonstrate that they have found a vulnerability that allows them to take control of or surreptitiously influence devices through the tiny accelerometers that are standard components in consumer products like smartphones, fitness monitors and even automobiles.
In their paper, the researchers describe how they added fake steps to a Fitbit fitness monitor and played a “malicious” music file from the speaker of a smartphone to control the phone’s accelerometer. That allowed them to interfere with software that relies on the smartphone, like an app used to pilot a radio-controlled toy car.
“It’s like the opera singer who hits the note to break a wine glass, only in our case, we can spell out words” and enter commands rather than just shut down the phone, said Kevin Fu, an author of the paper, who is also an associate professor of electrical engineering and computer science at the University of Michigan and the chief executive of Virta Labs, a company that focuses on cybersecurity in health care. “You can think of it as a musical virus.”
The flaw, which the researchers found in more than half of the 20 commercial brands from five chip makers they tested, illustrates the security challenges that have emerged as robots and other kinds of digital appliances have begun to move around in the world.
With dozens of start-ups and large transportation companies pushing to develop self-driving cars and trucks, undetected vulnerabilities that might allow an attacker to remotely control vehicles are an unnerving possibility.
Still, computer security researchers said the discovery was not a sky-is-falling bug but rather a revealing window into the cybersecurity challenges inherent in complex systems in which analog and digital components can interact in unexpected ways.
“The whole world of security is about unintended interactions,” said Paul Kocher, a cryptographer and a former executive at the chip company Rambus.
Accelerometers are instruments that measure acceleration and are frequently manufactured as silicon chip-based devices known as microelectromechanical systems, or MEMS. Accelerometers are used for navigating, for determining the orientation of a tablet computer and for measuring distance traveled in fitness monitors such as Fitbits.

In the case of the toy car, the researchers did not actually compromise the car’s microprocessor, but they controlled the car by forcing the accelerometer to produce false readings. They exploited the fact that a smartphone application relies on the accelerometer to control the car.
While toy cars might seem like trivial examples, there are other, darker possibilities. If an accelerometer was designed to control the automation of insulin dosage in a diabetic patient, for example, that might make it possible to tamper with the system that controlled the correct dosage.
Dr. Fu has researched the cybersecurity risks of medical devices, including a demonstration of the potential to wirelessly introduce fatal heart rhythms into a pacemaker.
He said the current research was inspired by a discussion in his group about a previous study in which drones were disabled with music. He added that earlier research demonstrated denial-of-service attacks that used sound to disable accelerometers.
In 2014, security researchers at Stanford University demonstrated how an accelerometer could be used surreptitiously as a rudimentary microphone, for example. And in 2011, a group from the Massachusetts Institute of Technology and the Georgia Institute of Technology demonstrated the use of an accelerometer in a smartphone to decode roughly 80 percent of the words being typed on a nearby computer keyboard by capturing vibrations from the keyboard.
In the case of the research by the University of Michigan and the University of South Carolina, scientists stopped the accelerometer from functioning and changed its behavior.
In testing 20 accelerometer models from five manufacturers, they affected the information or output from 75 percent of the devices tested and controlled the output in 65 percent of the devices.
The Department of Homeland Security was expected to issue a security advisory alert Tuesday for chips produced by the semiconductor companies documented in the paper, Dr. Fu said. The five chip makers were Analog Devices, Bosch, InvenSense, Murata Manufacturing and STMicroelectronics.
The paper, which will be presented at the IEEE European Symposium on Security and Privacy in Paris next month, also documents hardware and software changes manufacturers could make to protect against the flaws the researchers discovered.


0 comments:
Post a Comment